This morning I was greeted by a curious message in my Outlook inbox. My spidey sense immediately smelled a rat as I had never seen style of phishing attempt before. I initially opened it on my phone and couldn’t make out the headers to see if there was anything phishy so I opened it on my PC to inspect it.
This morning I was greeted by a curious message in my Outlook inbox. My spidey sense immediately smelled a rat as I had never seen style of phishing attempt before. I initially opened it on my phone and couldn’t make out the headers to see if there was anything phishy so I opened it on my PC to inspect it.
Now this is probably old news to anyone in IT or cyber security , but I thought I’d detail what I did and the clues that made it obvious that this was yet another phishing attempt that had got through Outlook’s filters. Suspicious bits are highlighted below:

- The poor formatting – the over-sized logo. Maybe not the best metric but something that should make you think twice before trusting it.
- The from address made to look like it came from an official Microsoft Outlook domain – “outlook.email.messages.com”. A quick ‘whois’ check on the second level domain component (messages.com) reveals that it has been registered via a third party in the Cayman Islands with the registrant details (deliberately) masked. Compare that to the Microsoft registered Outlook.com where the details of the registrant are transparent.
- Another phishy domain name I’m not familiar with. A quick whois reveals an unrelated third party. Googling the sdplanes.com domain name reveals links to a page that is currently offline or unavailable. It’s likely this firm has been the victim of a hack and their system abused to send the email / spoof the return address to allow it to pass our email spam filters.
- The attachment – the most obvious bit. Note how this is made to look like an audio attachment – the sender even took the trouble to insert a special character (audio speaker) at the start of the file name and .wav later on, but note the actual extension (the bit at the end of the file) is that of an html file. That will guarantee that the file will open in your browser if you double-click it.
- Addressing me by the local-part of my email address rather than my name is a clear sign that this has been gleaned by a bot rather than entered by a human. In other words, the sender likely does not know me.
- Poor spelling. Again not the best metric but definitely a warning sign that all is not well.
So what do I recommend if you receive suspicious mails with suspicious attachments?
Delete it!
If it’s important enough for the sender, they will contact you some other way. We all miss emails from time to time – they end up in spam when they’re not meant to, or we simply overlook them, the bottom line is none of us mere mortals are that important that we’re going to miss something huge that way, it’s more likely you’ll be the next victim of ID theft, malware or ransomware. Funny how our curiosity often trumps common sense. Somehow we manage to convince ourselves that we’re going to miss the lottery winnings if we don’t click that attachment. Delete it!
Now that said, what did I do? Of course I didn’t delete it. I’m way too curious.
The first thing was to save the attachment to my local drive and open it in my favorite text editor.
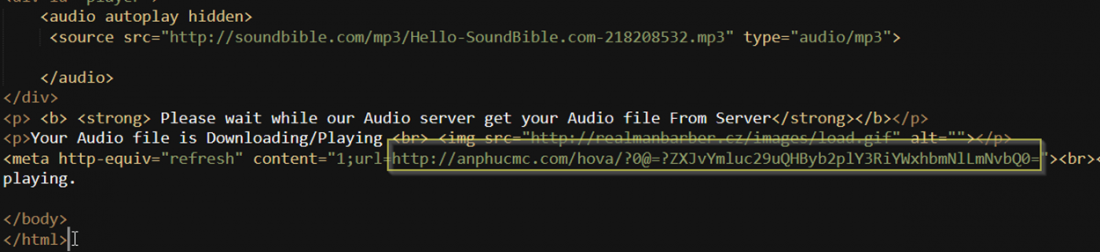
Note that meta http-equiv line which effectively refreshes and redirects to the highlighted URL.
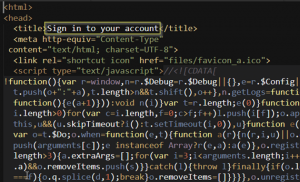
Using the same text editor, I opened that URL and got the main page the attacker wanted me to have open in my browser and what do you know – clearly a phishing page judging by that title:
The next job was to do my civic duty and let the owners / registrars of those various domain names gleaned above know that their services are being abused. I forwarded the original phishing mail, removed the attachment and composed a generic intro message to let them know what I knew, then put all those abuse@ email addresses gleaned from the ICANN whois lookups into the BCC field and hit send. My experience is that most decent services will act to ban the trolls / take down their content within 24 hours. Those who aren’t tech savvy and weren’t aware that their services had been hacked / being used for nefarious reasons are usually thankful for the heads up.
Stay safe!